Knowledge Base
TR-069 & USP Technical Documentation
Your complete technical reference for TR-069 CWMP protocol, USP platform, ACS server implementation, and network management best practices.
Technical Docs
📚 Knowledge Base Index
🔧 TR-069 Protocol
🚀 USP Platform
🔧 TR-069 Protocol Overview
TR-069 (Technical Report 069), also known as CWMP (CPE WAN Management Protocol), is the industry-standard protocol for remote management of Customer Premises Equipment (CPE) in broadband networks.
🎯 What TR-069 Enables
With TR-069, service providers can:
- 🔧 Auto-configure devices remotely without manual intervention
- 📊 Monitor performance and collect diagnostics in real-time
- 🔄 Deploy firmware updates across thousands of devices efficiently
- 🛠️ Troubleshoot issues remotely, reducing truck rolls and support costs
- 📈 Provision new services instantly and at scale
✅ Key Benefits
🧩 Core TR-069 Components
ACS (Auto Configuration Server): Central management platform
CPE (Customer Premises Equipment): Remote managed devices
SOAP/HTTP: Structured message communication
SSL/TLS: Encrypted authentication layer
🏗️ TR-069 Architecture
🏢 Auto Configuration Server (ACS)
The ACS is the central management platform responsible for provisioning, monitoring, and troubleshooting CPE devices. Its key roles include:
- Device Management: Centralized configuration and real-time status monitoring
- Firmware Management: Deployment of firmware upgrades and version control
- Service Provisioning: Automated delivery of new services (e.g., VoIP, IPTV)
- Diagnostics: Remote execution of tests and fault reporting
- Performance Monitoring: Collection of key metrics (e.g., signal strength, uptime)
📡 Customer Premises Equipment (CPE)
The CPE is the remote device implementing the TR-069 client. Typical devices include:
- Residential Gateways: Home routers, modems
- Set-top Boxes: IPTV, streaming hardware
- VoIP Devices: SIP phones, ATAs
- IoT Devices: Smart home hubs, industrial sensors
- Enterprise Equipment: Edge routers, switches
🔄 TR-069 RPC Methods
📤 ACS → CPE (Server-Initiated Methods)
GetParameterValues- Retrieve current parameter valuesSetParameterValues- Modify configuration parametersGetParameterNames- Explore parameter tree structureGetParameterAttributes- Get read/write/notify settingsSetParameterAttributes- Modify attributes of parametersAddObject- Add an instance to a multi-instance objectDeleteObject- Remove object instancesDownload- Trigger firmware or file downloadsUpload- Retrieve logs or config files from the CPEReboot- Reboot the CPE remotelyFactoryReset- Reset to factory settingsGetAllQueuedTransfers- View pending download/upload operationsScheduleInform- Schedule a future Inform sessionSetVouchers- Deliver service vouchersGetOptions- Retrieve device-supported optionsKicked- Trigger immediate session
📥 CPE → ACS (Client-Initiated Methods)
Inform- Send device status and eventsTransferComplete- Acknowledge completed downloads/uploadsGetRPCMethods- Return list of supported RPCsAutonomousTransferComplete- Unsolicited file transfer reportDUStateChangeComplete- App module (DU) installation/update eventAutonomousDUStateChangeComplete- Autonomous DU changes reported
📋 Inform Event Codes
| Code | Description |
|---|---|
0 | BOOTSTRAP – Initial connect after reset |
1 | BOOT – Device startup/reboot |
2 | PERIODIC – Regular interval check-in |
3 | SCHEDULED – Scheduled by ACS |
4 | VALUE CHANGE – Parameter change detected |
5 | KICKED – Remote trigger by ACS |
6 | CONNECTION REQUEST – ACS-initiated session |
7 | TRANSFER COMPLETE – Firmware/config downloaded |
8 | DIAGNOSTICS COMPLETE – Results from diagnostic tests |
9 | REQUEST DOWNLOAD – Device-initiated download |
10 | AUTONOMOUS TRANSFER COMPLETE – Unsolicited download complete |
M | Method-Specific Events – e.g., M Reboot, M Download |
🧭 TR-069 Implementation Guide
🎯 Planning Phase
- Network Assessment: Evaluate current network and CPE capabilities
- Device Inventory: Catalog TR-069-ready equipment
- Requirements Definition: Define use cases and KPIs
- Security Policy: Define encryption/authentication standards
- Scalability: Anticipate future growth and load
🔧 Technical Setup
- ACS URL Configuration: Define endpoint URLs on devices
- SSL Certificates: Secure all ACS/CPE communication
- Database Design: Model CPE data (parameters, logs)
- API Integration: Interface ACS with existing platforms (e.g., CRM, OSS)
- Monitoring Setup: Enable system health checks, alerts, and logs
🚀 Deployment
- Pilot Testing: Validate with a small CPE group
- Gradual Rollout: Expand in controlled waves
- Performance Monitoring: Track KPIs and system behavior
- Training: Prepare support and engineering teams
- Go-Live Support: Ensure 24/7 coverage during launch window
🔍 TR-069 Use Cases & Real-World Scenarios
🏠 Residential Use Cases
Wi-Fi Configuration
Remotely configure SSIDs, passwords, encryption types, and band steering.
Firmware Updates
Push firmware updates at scale to fix vulnerabilities or deliver new features.
Service Activation
Enable services like VoIP, IPTV, or parental controls remotely without user interaction.
Remote Troubleshooting
Diagnose issues such as low signal, unstable connection, or misconfigurations.
🏢 Enterprise Solutions
Branch Office Management
Centralize configuration for CPEs across all remote locations.
VPN Setup
Remotely configure secure VPN tunnels and routing rules.
QoS Policy Enforcement
Apply Quality of Service rules to prioritize mission-critical applications.
Compliance Auditing
Ensure configurations align with security and compliance standards in real time.
🔄 USP Migration Strategy
Migration Approaches
1. 🔄 Gradual Migration (Recommended)
Deploy USP alongside your existing TR-069 infrastructure and migrate devices and services incrementally:
- Phase 1: Deploy the USP Controller for new devices
- Phase 2: Migrate non-critical services to USP
- Phase 3: Upgrade eligible legacy devices with USP support
- Phase 4: Complete the migration and retire TR-069
2. 🚀 Parallel Operation
Run TR-069 and USP systems concurrently to minimize risk and ensure flexibility:
- Continue using TR-069 for legacy or unsupported devices
- Use USP for new services, smart home, and IoT deployments
- Transition gradually as devices reach end-of-life or firmware is upgraded
3. 🎯 Service-Based Migration
Migrate selectively based on business priorities, services, or customer segments:
- Start with IoT and smart home ecosystems
- Transition enterprise and high-value customers
- Focus on services that require real-time control or advanced security
🎯 Migration Benefits
Future-Proofing: Designed to support next-generation IoT and connected devices
Enhanced Security: Built-in support for TLS 1.2+, mutual authentication, and secure messaging
Real-Time Management: Event-driven architecture enables instant control and telemetry
Operational Efficiency: Reduces costs through automation and multi-controller support
❓ Frequently Asked Questions
🔧 TR-069 Questions
Q: What is the difference between TR-069 and CWMP?
A: TR-069 and CWMP refer to the same protocol. CWMP (CPE WAN Management Protocol) is the technical name defined by the TR-069 specification.
Q: How often should CPE devices contact the ACS?
A: Typically every 24 hours via periodic Inform messages, but this interval can be customized. High-priority devices may report more frequently.
Q: Can TR-069 work behind NAT or firewalls?
A: Yes. TR-069 is CPE-initiated, meaning no inbound firewall rules are required. The device initiates all communication to the ACS.
Q: What happens if the ACS is temporarily unavailable?
A: The CPE will retry connections using exponential backoff and queue events until the ACS becomes reachable again.
🚀 USP Questions
Q: Is USP backward compatible with TR-069?
A: Not directly. However, hybrid systems can manage both TR-069 and USP devices within the same ecosystem.
Q: When is the right time to migrate to USP?
A: USP is recommended for new deployments involving IoT, smart home, or applications needing real-time device management and extensibility.
Q: Does USP support all TR-069 features?
A: USP includes nearly all TR-069 capabilities, plus enhancements like real-time event subscriptions, multiple communication protocols, and improved security.
Q: Which protocol should I use for new projects?
A: USP is the preferred choice for new projects, especially those involving IoT, multi-controller environments, or rapid service deployment.
🛠️ Troubleshooting Guide
🔍 Common Issues
- Connection Failures:
- Verify ACS URL configuration
- Check SSL certificate validity and trust chain
- Ensure network connectivity
- Review firewall/NAT policies
- Authentication Errors:
- Confirm CPE credentials (username/password or certs)
- Check validity and expiration of device certificates
- Inspect ACS authentication logs
- Performance Issues:
- Monitor database load and query efficiency
- Check server resource usage (CPU, memory)
- Review ACS and device session logs
📊 Diagnostic Tools
- Log Analysis:
- ACS server logs
- CPE client logs
- Packet captures (e.g., Wireshark)
- SQL/database logs
- Testing Tools:
- TR-069 emulators or test clients
- SOAP/HTTP message validators
- Certificate inspection tools
- Connectivity and DNS tests
- Monitoring:
- Real-time dashboards
- Telemetry metrics (latency, response time, success rate)
- Alerting and threshold notifications
- Historical trend analysis
⚡ Quick Fixes
- CPE Not Connecting:
- Reboot the CPE
- Confirm the correct ACS URL is configured
- Verify internet access and DNS resolution
- Perform a factory reset if necessary
- Slow System Performance:
- Optimize database queries and indexing
- Use connection pooling and caching mechanisms
- Allocate more memory/CPU to ACS services
- Check for background tasks or overloaded components
- Certificate Problems:
- Renew expired certificates
- Verify certificate chain and trust store
- Ensure NTP time sync is accurate
- Update root/intermediate CAs if required
🚀 USP (User Services Platform)
USP (User Services Platform) is the next-generation protocol defined in TR-369, designed to overcome the limitations of TR-069. It enables real-time, secure, and scalable management of modern connected devices, including IoT, residential gateways, and enterprise equipment.
🌟 Key Advantages of USP
- 🌐 Multi-Protocol Support: Supports STOMP, MQTT, WebSockets, and CoAP for flexible transport options
- 🏗️ Multi-Controller Architecture: Multiple entities can manage different aspects of a single device
- 🔒 Enhanced Security: End-to-end encryption, certificate-based authentication, and secure key management
- 📱 IoT Ready: Optimized for low-power and constrained devices
- ⚡ Real-Time Messaging: Instant event-driven communication without polling
- 🔄 Subscription-Based Events: Devices can subscribe to and push updates as they happen
USP Protocol Stack
🌐 USP Protocol Stack Overview
USP is transport-agnostic and can operate over several modern communication protocols:

Simple Text Oriented Messaging Protocol
- Message queuing support
- Reliable delivery with acknowledgment
- Transactional messaging for state consistency

Message Queuing Telemetry Transport
- Lightweight and ideal for IoT environments
- Publish/Subscribe messaging model
- Quality of Service (QoS) levels for reliability

WebSockets
Bidirectional Real-Time Transport over HTTP
- Full-duplex communication
- Low latency and minimal overhead
- Compatible with modern browsers and web platforms
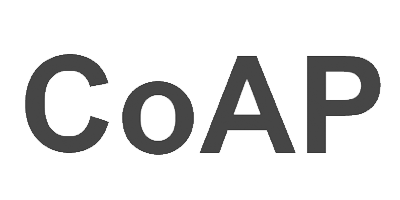
Constrained Application Protocol
- UDP-based protocol with RESTful interaction
- Low overhead for constrained devices
- Suitable for battery-powered sensors and IoT
🚀 USP Key Benefits
Multi-Controller Architecture
USP enables multiple management controllers (e.g., service provider, subscriber, third-party) to manage different functions of the same device simultaneously — promoting modularity and distributed service delivery.
Real-Time Events & Subscriptions
Built on an event-driven architecture, USP eliminates polling by enabling real-time push notifications, dynamic subscriptions, and live status updates.
End-to-End Security
USP enforces modern security mechanisms including:
- TLS 1.2+ with strong cipher suites
- Mutual authentication with client/server certificates
- Encrypted message payloads and trusted controller registration
TR-069 vs USP Comparison
📊 TR-069 (CWMP)
- ✅ Mature Technology: 15+ years in production
- ✅ Wide Device Support: Thousands of certified devices
- ✅ HTTP/SOAP Based: Well-understood protocols
- ✅ Proven Reliability: Battle-tested in large networks
- ⚠️ Single Transport: HTTP only
- ⚠️ Polling Based: Regular inform intervals
- ⚠️ Limited Multi-tenancy: Single ACS per device
🚀 USP
- ✅ Multi-Protocol Support: STOMP, MQTT, WebSockets, HTTP
- ✅ Multi-Controller: Multiple management entities
- ✅ Event-Driven: Real-time push notifications
- ✅ Enhanced Security: Modern encryption standards
- ✅ IoT Optimized: Lightweight for constrained devices
- ✅ Cloud-Native: Designed for microservices
- ⚠️ Newer Standard: Growing device ecosystem
� Security & Performance Best Practices
🔒 Security Best Practices
- Always Use HTTPS: Ensure all TR-069 and USP communications are encrypted using HTTPS/TLS.
- Certificate Management: Implement a strong Public Key Infrastructure (PKI), enforce certificate expiration, and automate certificate rotation.
- Strong Authentication: Use certificate-based mutual authentication between CPEs and ACS/Controllers whenever possible.
- Access Control: Enforce role-based access controls (RBAC) to restrict administrative privileges in the ACS or USP Controller.
- Firmware Integrity Validation: Validate firmware images using checksums or digital signatures before deployment.
- Network Segmentation: Separate management-plane traffic from user-plane traffic via VLANs or dedicated interfaces.
- Regular Patching: Keep all platform components—ACS, database, web server, OS—up to date with the latest security patches.
- Audit Logging: Log all configuration changes, logins, and remote actions for compliance and security audits.
⚡ Performance Optimization Best Practices
- Database Optimization: Implement connection pooling, proper indexing, and query optimization to reduce load and latency.
- Caching Strategy: Use caching mechanisms (e.g., Redis) to store frequently accessed device data and reduce database reads.
- Load Balancing: Distribute incoming traffic across multiple ACS or USP Controller instances using reverse proxies or load balancers.
- Session Management: Tune TR-069 session duration and inform intervals to balance responsiveness and overhead.
- Bulk Parameter Operations: Combine multiple parameter updates into a single session to reduce round trips and improve efficiency.
- Monitoring & Alerting: Deploy real-time monitoring for CPU, memory, network, and session performance. Integrate with alerting systems (e.g., Prometheus + Grafana, ELK stack).
- Capacity Planning: Track device fleet growth and perform resource forecasting to proactively scale infrastructure.
- Scheduled Maintenance: Regularly perform database cleanups, log rotation, and system tuning to maintain optimal performance.
✅ Implementation Success
These practices ensure your device management infrastructure remains secure, responsive, and future-ready.
✅ Testing & Validation Best Practices
In broadband environments, rigorous testing is essential to ensure device stability, service reliability, and protocol compliance before large-scale deployment. A structured validation process reduces the risk of field issues and accelerates time-to-market.
🧪 Key Testing Areas
📋 Protocol Compliance Testing (TR-069 / USP)
Validate that CPEs comply with TR-069 or USP standards — including supported RPCs, session behavior, and message structure.
🗂️ Data Model Verification (TR-181 / TR-098)
Ensure that device parameters follow the correct schema: data types, access levels, notification flags, and tree structure.
🔄 Firmware Regression Testing
Test device behavior after firmware upgrades to verify that existing features still function correctly.
⚡ Performance & Load Testing
Simulate thousands of CPEs to evaluate the ACS or USP controller's ability to handle high concurrent loads.
🏋️ Stress & Endurance Testing
Execute long-duration and repetitive tests to uncover memory leaks, performance degradation, or crash conditions.
⚠️ Negative Testing & Fault Injection
Inject malformed requests, drop connections, or simulate timeouts to test error handling and recovery logic.
🤝 Interoperability Testing
Validate consistent behavior across different CPE models, vendors, and firmware versions in a mixed device environment.
🔧 Service Provisioning Scenarios
Test real-world use cases like remote Wi-Fi configuration, VoIP setup, or VPN provisioning via ACS or USP.
💡 Why AcsFlow Makes the Difference
🧠 AcsFlow's built-in testing engine automates all critical validation workflows — from protocol compliance and firmware certification to large-scale stress testing — empowering operators to qualify devices faster, ensure production readiness, and deliver more reliable broadband services.
Ready to implement ACS Server?
AcsFlow provides complete TR-069 and USP solutions with enterprise-grade features, expert support, and seamless deployment.